Perception Point’s security research team has identified an alarming new phishing campaign. Attackers are abusing Microsoft Office Forms to launch sophisticated two-step phishing attacks. Office Forms, typically used for creating surveys and quizzes, are now being leveraged by threat actors to trick targeted users into divulging their Microsoft 365 (M365) credentials.
“Form” Phishers With Love
Attackers create legitimate-looking forms on Microsoft Office Forms, embedding malicious links within the forms. These forms are then sent to targets en-masse via email under the guise of legitimate requests such as changing passwords or accessing important documents, mimicking trusted platforms and brands like Adobe or Microsoft Sharepoint document viewer.
Threat actors often use the email accounts of breached business partners and vendors to deliver two-step phishing attacks across supply chains, a tactic known as “external account takeover” or vendor email compromise.
How It Works
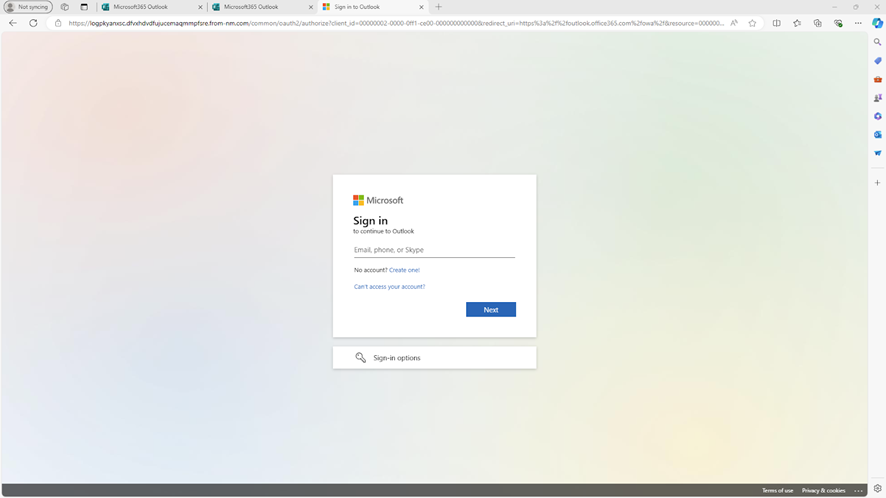
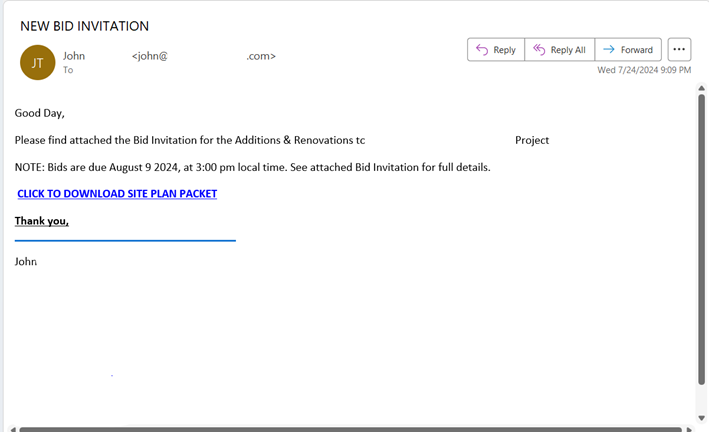
- Email Message: The victim receives an email with a link to a Microsoft Office Form.
- Form: The form hosted on a legitimate service appears authentic, requesting the user to click a link to view a document and fill out the questionnaire.
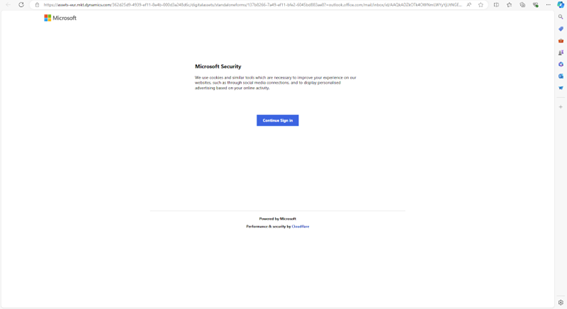
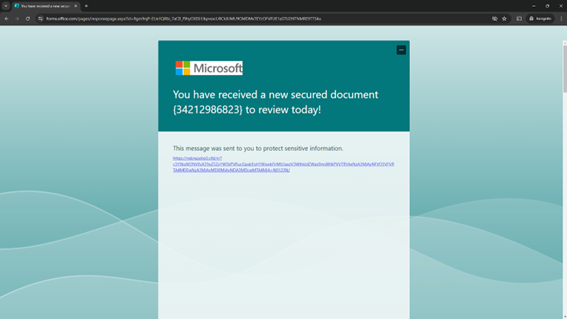
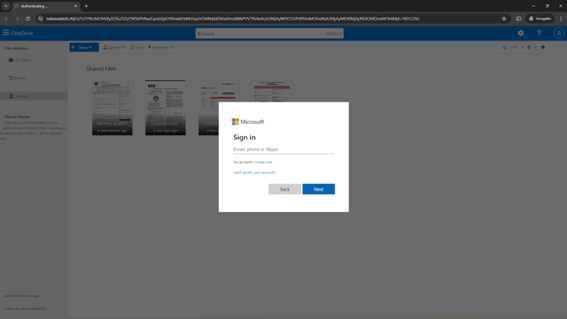
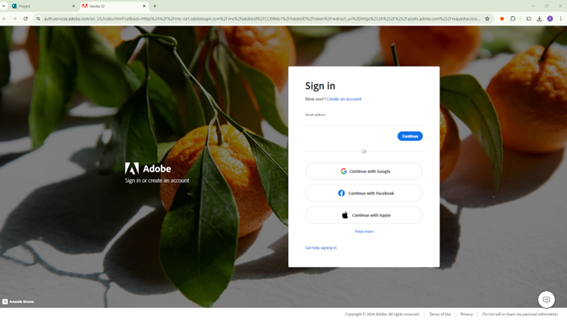
- Redirect: Clicking the link leads the user to a fake login page, such as a Microsoft 365 or Adobe account page, designed to harvest credentials.
Attackers enhance their forms’ credibility
by using convincing page titles and known favicons. Favicons are
small icons displayed in the browser tab, and by using Microsoft familiar
icons, attackers increase the perceived legitimacy of their fake pages. These
visual cues can easily trick users into believing they are on a genuine
Microsoft site.
Combined with the legitimate https://forms.office.com URL, the
attackers achieve a convincing “look and feel” of a Microsoft page.
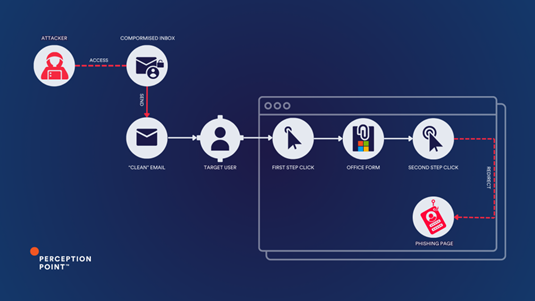
The Two-Step Phishing Kill Chain
In a two-step phishing attack, the attacker first gains access to a legitimate email account and sends targeted emails from this compromised account. These messages appear trustworthy, prompting recipients to click on a link that leads to a legitimate website. This is the first step, where the attacker uses the high reputation of legitimate sites like Office Forms, Canva, and many others to evade detection.
The second step occurs when the user clicks another link on the legitimate site, redirecting them to a spoofed page designed to steal credentials.
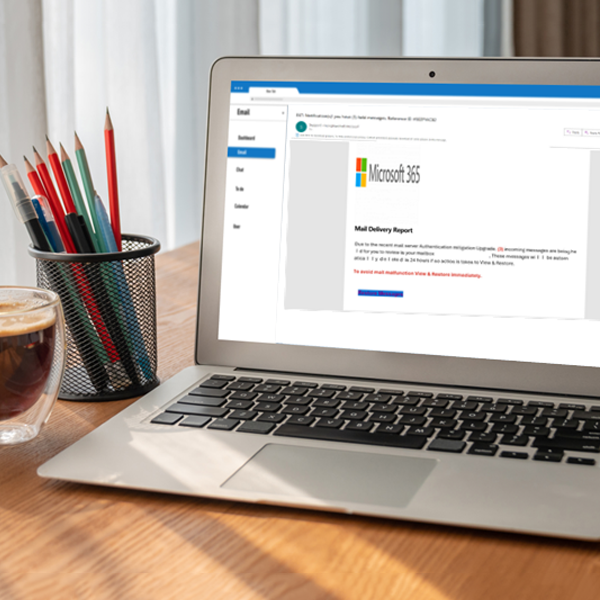
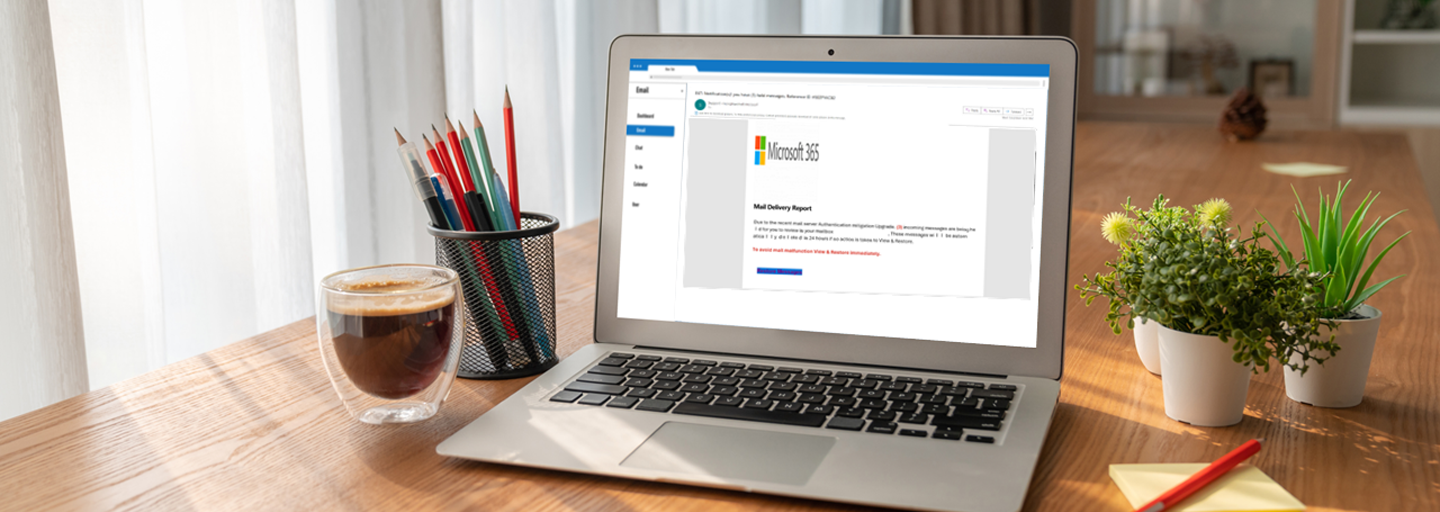
Example 1:
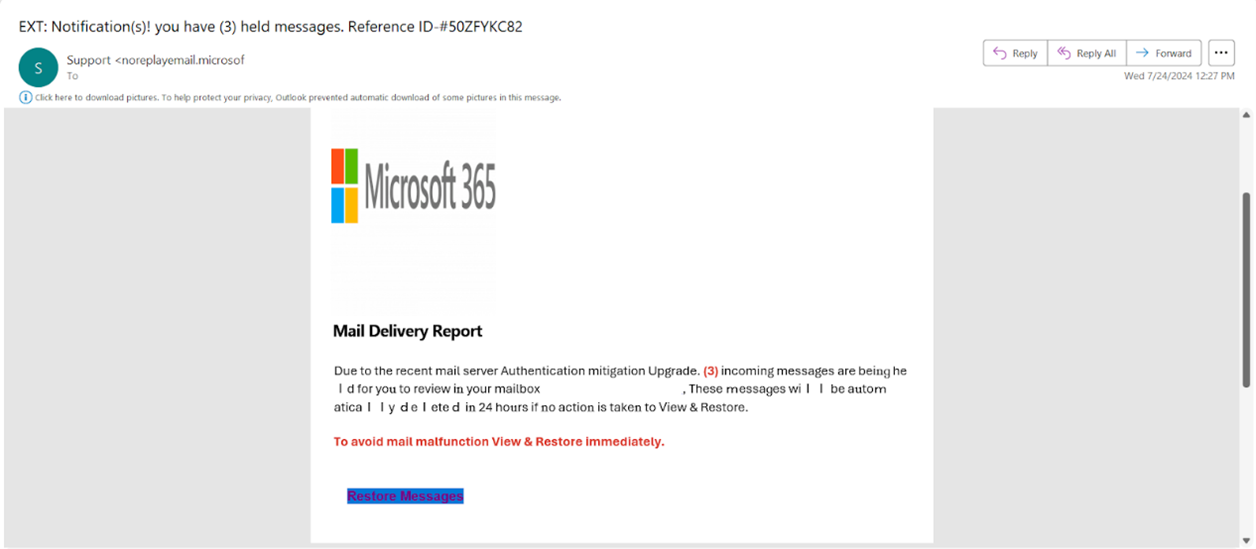

Example 2:
Why Two-Step Phishing Evades Gateways and Native Detection (Microsoft Defender)
- Legitimate Origin: The attack originates from compromised legitimate accounts, making it difficult for email security solutions to flag the emails as malicious.
- Familiarity: Recipients are more likely to trust and engage with emails from known senders, increasing the attack’s success rate.
- High Reputation Sites: The first link often leads to a high-reputation site, bypassing security filters. The malicious intent only becomes apparent at the second stage.
How Perception Point Prevents These Forms-Gone-Wrong
Perception Point employs an advanced object detection model to counter two-step phishing attacks. This model takes a screenshot of each webpage and identifies clickable elements, simulating the victim’s interaction. The model follows each link and analyzes the subsequent pages for malicious content. This approach ensures that even if the initial link appears benign, any malicious payload in subsequent steps is detected and blocked.
Artigo traduzido e disponibilizado pela DigitalSkills Consulting - Distribuidora oficial de soluções de cibersegurança do fabricante Perception Point. Para mais informações: www.digitalskills.pt | [email protected] | 21 418 05 21
Artigo original no site do fabricante em https://perception-point.io/blog/two-step-phishing-campaign-exploits-microsoft-office-forms/