In recent months, threat actors have discovered a troubling new method to exploit URL rewriting, a feature intended to protect users by replacing links in emails. By manipulating these rewritten URLs, attackers mask highly evasive phishing links behind trusted domains of security vendors, effectively bypassing detection. This abuse has led to a critical surge in advanced phishing attacks that leverage the very tools developed to prevent them.
Threat actors who specialize in phishing are
always seeking the most effective methods to deliver their malicious links via
email messages. In recent years, we’ve witnessed the rise of new tactics such
as QR
code phishing (a.k.a. “quishing”) and two-step delivery methods that
disguise malicious links behind legitimate services like Canva or Office
Forms. These techniques aim to evade both legacy and AI-powered email
security solutions. However, since mid-June 2024, a highly alarming trend has
emerged – attackers are now turning email security against itself,
exploiting URL rewriting features designed to prevent
phishing threats. It’s a poetic quid pro quo, but not the kind
defenders would necessarily appreciate.
To understand how attackers are increasingly abusing these features, let’s
first break down what “URL rewriting” actually is.
What is URL Rewriting?
Different email security vendors may call it by various names (URL protection, click-time-protection, etc.) but URL rewriting serves a singular goal: protecting users from malicious links embedded in emails. The process at its core is quite similar between vendors and involves replacing original URLs with modified links that direct the recipient first to the vendor’s servers. There, the links are scanned for threats when clicked – if deemed safe, the recipient can access it and is redirected to the web content, if not it will get blocked.
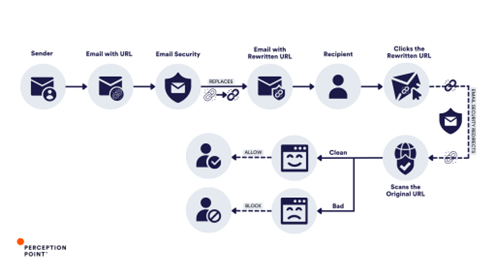
There are two main paradigms for URL Rewriting:
- Legacy security solutions rely on rules and signatures that are based on previously identified threats. These solutions rewrite URLs so that they can assess the link later, leveraging updated threat intelligence and their broad visibility to email traffic. This approach allows them to block a site if new information becomes available – often, unfortunately, after an initial victim has already been hit and reported back to them (“patient zero”).
- The newer approach to URL rewriting is a bit more proactive. It scans links at the time of the click, using technologies like computer vision and machine learning algorithms. Unlike legacy systems, these solutions don’t just rely on known malicious attacks or threat intelligence databases but also evaluate the URL’s behavior in real-time.
Sometimes, organizations use a combination of the two.
For instance, a company might employ a Secure Email Gateway (SEG) like Proofpoint or Microsoft Defender’s native “Safe Links” feature while also using an ICES (Integrated Cloud Email Security) solution for extra protection. In such cases, the ICES solution might embed its rewritten link within the first layer’s rewritten link, let’s call it a “double rewrite.” However, this complexity doesn’t always result in “double protection”.
Much like you do right now reading this blog, attackers too have studied the inner workings of URL rewriting, and now, they exploit it. This has led to an increase in phishing attacks where the very tools designed to protect users against phishing are being used against them.
Lemons to Cyber Lemonade: the URL Rewriting Abuse
Over the past 3 months, Perception Point security researchers have observed a dramatic surge in phishing attacks exploiting the URL protection services of trusted, legitimate email security vendors – SEG and ICES alike. Such well-crafted campaigns have already targeted hundreds of organizations worldwide, potentially impacting many more.
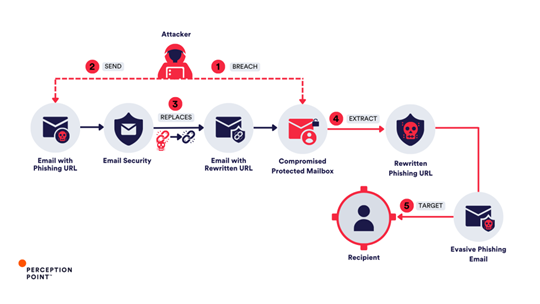
To abuse URL rewriting, attackers typically have 2 theoretical options. The less likely possibility requires gaining access to internal encryption systems of an email security vendor to rewrite phishing URLs directly. However, the more probable tactic is for attackers to first compromise legitimate email accounts protected by a URL rewriting feature and then to send an email to themselves containing their “clean-later-to-be-phishing” URL. Once the email passes through the URL protection service, the link is replaced, and includes the email security vendor’s name and domain, giving it an extra layer of legitimacy. Some email security services, in an effort to save on resources, often whitelist their own dedicated rewriting domains (e.g. protect/defend*name of vendor*.com), which plays directly into the attackers’ hands when they target users protected by specific vendors they abused.
This “branded” rewritten URL is later weaponized. After it has been “whitelisted” by the security service, the attackers can modify the destination of the URL to redirect users to a phishing site. This technique allows the malicious link to bypass further security checks, as many services rely on the initial scan and do not rescan known URLs. As an alternative course of action, attackers often employ advanced evasion techniques such as CAPTCHA evasion or geo-fencing to circumvent even a thorough analysis by the email security vendor.
This manipulation of URL rewriting is particularly dangerous because it takes advantage of the trust that users place in known security brands, making even highly aware employees more likely to click on the seemingly safe link. The threat actors exploit the gap between the time a URL is rewritten and when it is weaponized, bypassing most traditional security tools.
Artigo traduzido e disponibilizado pela DigitalSkills Consulting - Distribuidora oficial de soluções de cibersegurança do fabricante Perception Point. Para mais informações: www.digitalskills.pt | [email protected] | 21 418 05 21